What is C2PA Manifest?
A C2PA manifest is the digital "birth certificate" of content - a comprehensive record that travels with digital files to prove their authenticity, track their history, and verify their integrity.
Understanding C2PA Manifest Structure
Think of a C2PA manifest like a detailed passport for digital content. Just as a passport contains your photo, personal information, and stamps from countries you've visited, a C2PA manifest contains:
- Content identity: Cryptographic hashes that uniquely identify the content
- Provenance claims: Assertions about who created the content and when
- Editing history: A record of modifications, like stamps in a passport
- Technical metadata: Camera settings, software versions, and creation tools
- Digital signatures: Cryptographic proof that prevents tampering
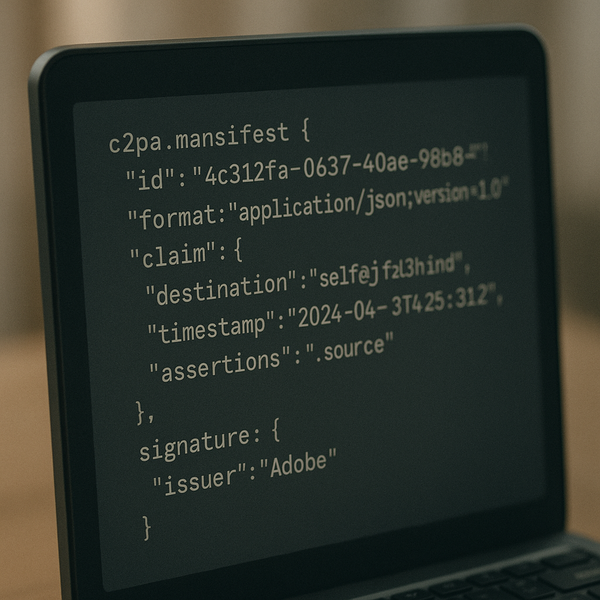
The Anatomy of a C2PA Manifest
A typical C2PA manifest is structured in several key sections:
1. Header Information
The manifest starts with basic metadata including the format version, creation timestamp, and the type of content it's protecting. This ensures compatibility and provides context for processing tools.
2. Claim Store
The heart of the manifest is the claim store, which contains assertions about the content:
- Hard binding: Links the manifest to specific content through cryptographic hashes
- Ingredient assertions: Information about source materials used to create the content
- Action assertions: Records of editing operations performed on the content
- Metadata assertions: Technical details about creation tools and settings
3. Digital Signatures
Each claim in the manifest is protected by digital signatures that use public key cryptography. These signatures ensure that any tampering with the manifest can be detected, maintaining the integrity of the provenance information.
4. Certificate Chain
The manifest includes certificates that validate the identity of the signing entity. This creates a chain of trust back to recognized certificate authorities, similar to how websites use SSL certificates.
How Manifests Track Content History
One of the most powerful features of C2PA manifests is their ability to maintain a complete history of content modifications. Here's how it works:
Example: Photo Editing Journey
- Original capture: Camera creates initial manifest with shooting metadata
- Import to editor: Software adds action assertion about file import
- Color correction: New action assertion records the specific adjustments made
- Crop operation: Another assertion documents the cropping parameters
- Export: Final assertion records output format and compression settings
Types of Information in Manifests
Creator Information
Manifests can include details about the content creator, such as:
- Digital identity certificates
- Organization affiliations
- Contact information (optional)
- Social media handles or website URLs
Technical Metadata
Rich technical information helps verify authenticity:
- Camera make, model, and firmware version
- Lens information and shooting parameters
- GPS coordinates (if enabled)
- Software versions and plugin information
- AI or machine learning tool usage
Content Ingredients
For composite content, manifests track all source materials:
- Stock photos or graphics used
- Audio tracks in video content
- Text elements and fonts
- AI-generated components
How to Verify C2PA Manifests
While manifests contain complex technical information, modern tools make them accessible:
- Verification tools: Like our C2PA Viewer that parse and display manifest data
- Browser extensions: That show C2PA information for web images
- Professional software: Creative applications with built-in C2PA support
- API integrations: For developers building verification into their applications
Privacy and Security Considerations
C2PA manifests are designed with privacy in mind:
- Personal information inclusion is optional and controlled by the creator
- Location data can be stripped or generalized
- Cryptographic techniques protect against forgery
- Manifests can be removed if privacy concerns arise
Explore C2PA Manifests
Upload your own C2PA-enabled content to see manifest data in detail with our verification tool on the homepage.
View Analyzer Tool →